Caesar Cipher & Mono Alphabetic Ciphe In Cryptography?
Hello Friends, In this blog post(Caesar Cipher & Mono Alphabetic Cipher) I am going to let you know about the Caesar cipher and Mono Alphabetic cipher.
Before going to explain this I want to provide you with a small introduction to cipher or ciphertext so that those can also understand who are unaware of cipher and ciphertext.|Caesar Cipher & Mono Alphabetic Cipher|
A cipher is a text and or encrypted text that is made after applying an encryption algorithm or certain rule to a plain text.| Caesar Cipher & Mono Alphabetic Cipher|
So ultimately Cipher is the converted, encrypted text that generally gets decrypted when it finally reaches the receiver.|Caesar Cipher & Mono Alphabetic Cipher|
Types of Cipher :
Caesar Cipher:
The earliest known use of a substitution cipher, and the simplest, was by Julius Caesar.
The Caesar cipher involves replacing each letter of the alphabet with the letter standing three places further down the alphabet for example:
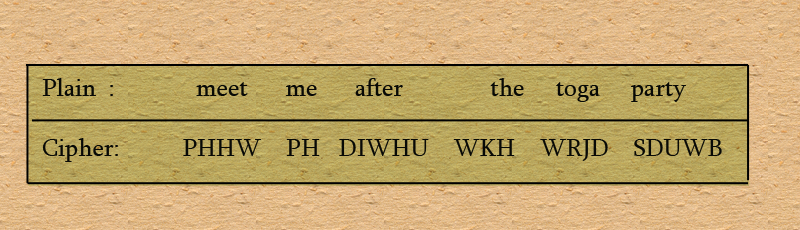
Note that the alphabet is wrapped around so that the letter following Z is A.
We can define the transformation by listing all possibilities as follows.
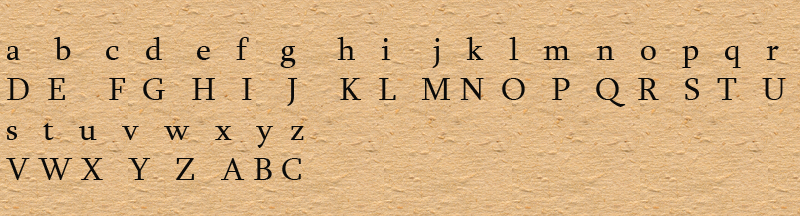
Let us assign a numerical equivalent to each letter.

Then the algorithm can be expressed as follows. For each plaintext letter P, Substitute the ciphertext letter C:
C = E(p) = (p+3)mod(26)
A shift may be of any amount so that the general Caesar algorithm is
C = E (p) = (p+k)mod(26)
Where k takes on a value in the range of 1 to 25. The decryption algorithm is simply
p = D (c) = (C-k) mod 26
If it is known that a given ciphertext is a Caesar cipher, then brute force cryptanalysis is easily performed.
Mono Alphabetic Cipher:
With only 25 possible keys, the Caesar cipher is far from secure.
A dramatic increase in the keyspace can be achieved by allowing an arbitrary substitution.
Recall the assignment for the Caesar cipher:
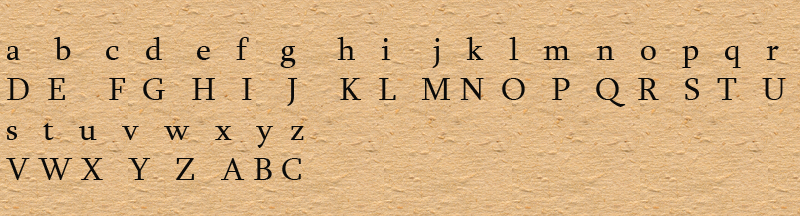
If instead, the ‘cipher’ line can be any permutation of the 26 alphabetic characters, then there are 26! or greater than 4 X 10pow26 possible keys.
This is 10 orders of magnitude greater than the keyspace for DES and would seem to eliminate brute-force techniques for cryptanalysis.
Such an approach is referred to as a monoalphabetic substitution cipher because a single cipher alphabet(mapping from the plain alphabet to the cipher alphabet) is used per message.
An important point to note about this technique is that any letter in the plain text can be replaced by a pre-decided letter from the alphabet.
Since the substitution is random, thus the attacker can not easily find any relationship between the letters in the ciphertext, this is more effective than the Caesar cipher technique.
आप नीचे दिए हुए कुछ इम्पोर्टेन्ट ब्लॉग लिंक्स को भी पढ़ सकते है |
What is Ethernet….?
Difference between token ring, Ethernet, and token bus networks….?
What is a token ring….?
OSI Model In Hindi…
Classless Addressing vs Classful Addressing In Hindi…
Internet Security Threats…
Dijkstra’s Algorithm: Shortest Path Routing Algorithm…
Caesar Cipher & Mono Alphabetic Cipher…
What are the types of network security…
SMTP: Simple Mail Transfer Protocol…
What Is VPN: Virtual Private Network…
HTTP: HyperText Transfer Protocol…
Token Bus In Hindi…
Quick Q&A:
What is a monoalphabetic cipher in cryptography?
In monoalphabetic cipher, each occurrence of plaintext is replaced by a corresponding ciphertext symbol to create a new ciphertext.
The key for this may be a table of correspondence or any other function which this correspondence is being computed from.
What is Caesar’s cipher in cryptography?
We can also call it a type of substitution cipher.
To build this type of cipher each letter of the plaintext is replaced by another letter.
And this replaced letter can be found with the cipher formula that we decided to make our ciphertext.
For example, with a right shift of 3, A would be replaced by D, and B would be replaced by E, and so on.
You can make any formula as per your requirement.
What are the different types of ciphers in cryptography?
The few most common ciphers used in cryptography are listed below:
Substitution ciphers: Replace bits, characters, or character blocks in plaintext with alternate bits,…
… characters, or character blocks to produce ciphertext.
Transposition ciphers.
Polygraphic ciphers.
Permutation ciphers.
Private-key cryptography.
Public-key cryptography.
In the case of any queries, you can write to us at a5theorys@gmail.com we will get back to you ASAP.
Hope! you would have enjoyed this post about Caesar cipher and Mono Alphabetic Cipher.
Please feel free to give your important feedback in the comment section below.|Caesar Cipher & Mono Alphabetic Cipher|
Have a great time! Sayonara!


